WannaCry: Nothing New Here Apart from a Catchy Name
by Sash, on 17/05/2017 1:17:00 PM
Even the catchy name is not particularly innovative (Heartbleed has to take that prize over others such as BEAST and POODLE).
As someone intimately involved in cyber security on a daily basis, I cannot understand why some events get so much attention whilst much more fundamentally-important issues remain off the radar of the C-suite who actively manage business risk.
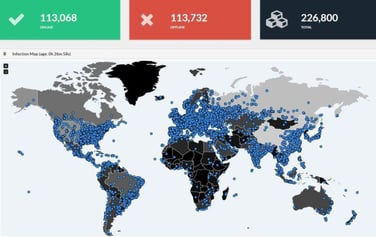 Over the weekend we have a two month old exploitable vulnerability that was used to exploit unpatched assets. If I had a thousandth of a bitcoin for every time that has occurred I would be writing this from my superyacht moored off the south of France.
Over the weekend we have a two month old exploitable vulnerability that was used to exploit unpatched assets. If I had a thousandth of a bitcoin for every time that has occurred I would be writing this from my superyacht moored off the south of France.
OK so I'll acknowledge those not from an IT background may find the fact that the exploit was part of an NSA toolkit interesting. Sure it is, but it's just another vulnerability in a database of hundreds of thousands. The impact was significant, but that is often the case. The Renault Formula 1 team was also compromised during a race weekend which reportedly affected their lap times during qualifying. I find that interesting but I'm sure there are plenty of interesting risk realisation scenarios for any number of vulnerability exploitation scenarios.
I've presented to rooms full of professionals who have just heard from vendors about how terrific their products are, and how they will solve all of their worldly (cyber security) problems, and I tell them to ignore all of that and focus on getting the basics right, one of which is vulnerability management. The rest falls into place after that. It's not rocket science - it's barely any science - malicious actors use vulnerabilities to compromise an environment, so how about focussing on the mechanism that enables the exploitation.
It's hardly anything new either. David Jones and Kmart were compromised due to an unpatched WebSphere vulnerability, something a scheduled external scan should have identified. The curious programming "feature" related to the domain used to sinkhole it made it even more interesting, with the David vs Goliath story of a young researcher stopping a global spread of malware. Interesting, but it's really just another strain of ransomware using a recent vulnerability to spread, sprinkled with some "NSA" here and some "kill-switch" there.
The only thing that makes me wanna cry is the reactive nature of the industry to a problem that is consistent and ever-present, but which can be solved with fundamental risk management rather than your latest APT-cloud-machine-learning-adaptive-heuristic-HTML5dashboard-hybrid-killhain-threat-intel-broad-spectrum shiny new cyber toy.
For a 'matched' music selection (think matching wines) you may consider Australia's very own Keith:
.png?width=400&height=53&name=logo%20(1).png)

.png?width=423&height=56&name=logo%20(1).png)