A cyber security maturity assessment encompasses traditional information security risk assessments and “health checks” – allowing a business to get a clear view of their current security posture, to understand where they need to improve to meet their customised requirements, as well as what isn’t needed, and what steps they can take to become more secure.
Need to understand the risk to your business from the gaps in your information and cyber security policies and procedures? Or are you required to meet a certain framework in response to a 3rd party risk requirement, regulatory body, or tender submission?
At Security Centric our team of consultants and engineers work with you to help you understand the greatest cyber security risks in your specific environment, and then provide you with a roadmap of improvement measures that suit your business needs.
A cyber security maturity assessment helps you to get visibility over and understand the information security risks that your business is facing, and how these can be remediated.
For many companies that are looking to act as 3rd party suppliers, a maturity assessment alongside a comprehensive risk register helps to provide assurances to vendors, clients, and customers that you’re a risk-based organisation who make taking care of your customer’s data a priority. Increasingly businesses are looking at this as a requirement when deciding which 3rd parties to hire.
For some businesses this may be a requirement as part of providing assurances for your senior management or board that risks are being understood and mitigated as needed.
Cyber Maturity Assessments aren’t new. They’re the baseline for a lot of companies looking to uplift their security, however most consulting firms only assess risk based on a singular framework which may not be relevant to your business. At Security Centric, we look first at what types of standards your business needs to reach, taking a business risk approach across multiple frameworks. This may include adhering to a specific framework or selecting a hybrid approach to better suit your business’ requirements.
Frameworks our engineers work with include:
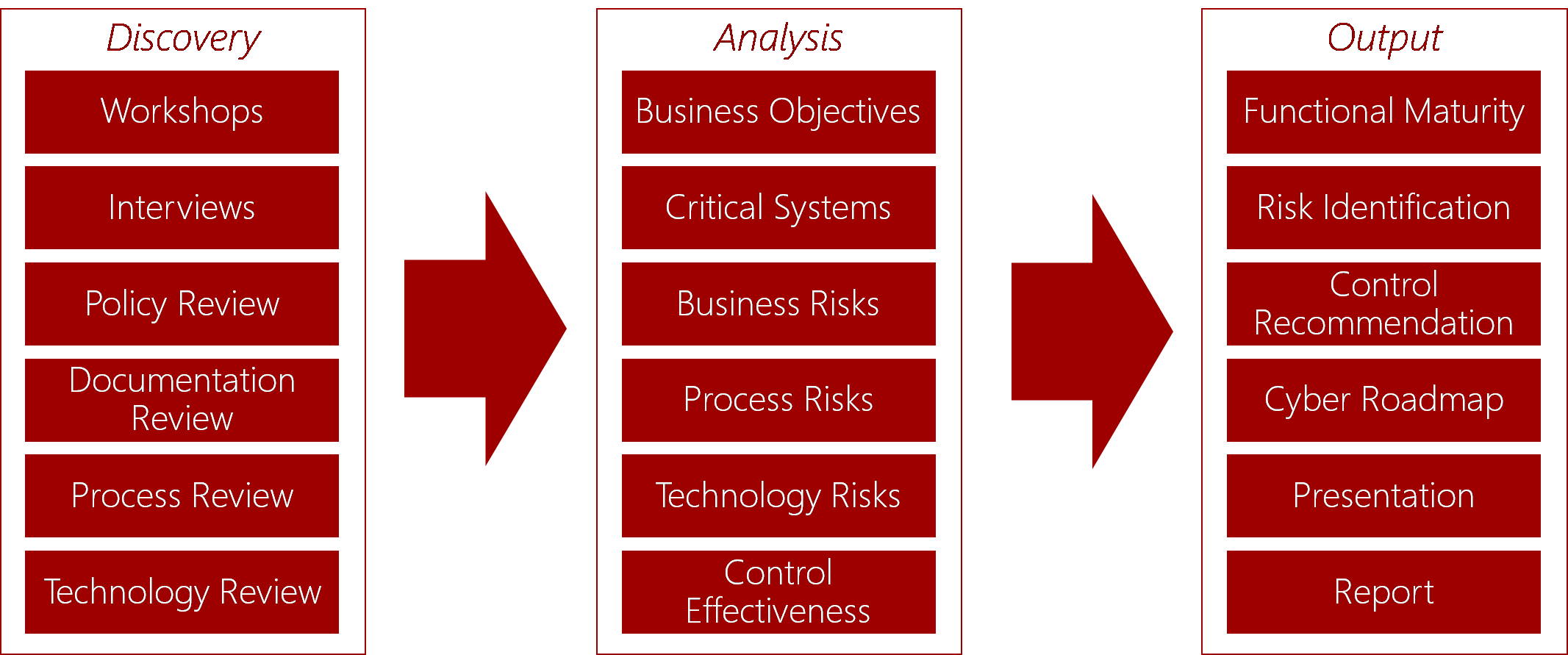
This service begins with a detailed series of questions to enable a comprehensive view of your existing security environment as well as a full understanding of your unique business needs. This may be based on a pre-existing needed outcome, or upon discovered needs with the help and guidance of our experts.
From there, our team assesses and analyses your current security posture as it is comparative to where it needs to be - with a focus on business objectives, critical systems, identified risks, and control effectiveness.
At the end of the assessment process, you’ll be provided with a gap analysis and risk assessment, along with a suggested remediation roadmap and options for ongoing support from our team of engineers – with an emphasis on a better use of your existing technologies, and addressing the highest impact and risk areas in a way that’s appropriate to your business.
We know cyber security can be confusing, but it doesn't have to be. If you've got questions about how you can improve your cyber and information security, our team of business and technical experts are happy to help.
Level 34, 201 Elizabeth St
Sydney, NSW 2000
Call us: +61 2 9199 0000