Understanding Your Outsourced Providers: IT Security MSSPs vs IT MSPs
by Security Centric, on 18/08/2021 4:01:02 PM
If you were to ask us what the main cybersecurity mistakes organisations routinely make were, the one where businesses rely on their everyday IT team or providers to also perform security-related tasks would be one of the least obvious, yet most concerning. Of the security operations or strategy conversations that we've had with our clients, prospects, and partners over the past nine years, the topic of the importance of ensuring IT security focused experts are engaged to work on their environments is one that comes up often.
Why it Matters:
Sometimes, understanding technology providers can be a lot like looking at one of those "spot the difference" puzzles. On the surface some things may be glaringly obvious - but others are more difficult to differentiate between. Overall, understanding how these two different sides of IT work together will help your organisation to become more secure and allow you to allocate technology budget in ways that help you perform better with less risk.
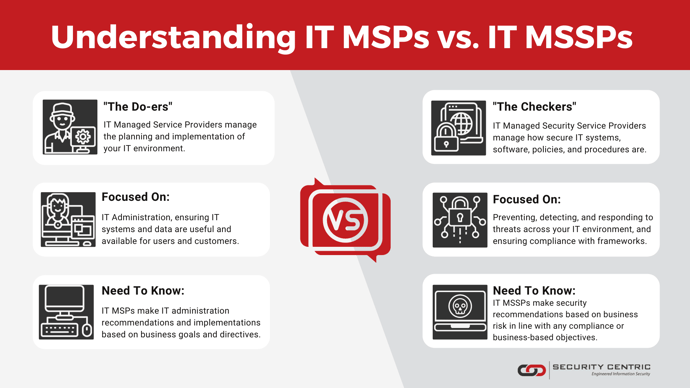
The key concept to understand in this rapidly changing digital infrastructure landscape is that businesses should not be relying on IT Managed Service Providers (MSPs) or staff to be focused on IT security. The specialisation that IT security now requires in order to keep up to date with the latest recommendations, regulations, controls, attack vectors, and threats is very different from traditional IT provider work. Whereas your IT MSP's main focus is on your IT administration, ensuring that your systems and data are useful and available to internal and external stakeholders.
Same Coin - Two Sides:
We can think of it in terms of IT providers being the “do-ers”, that is, they get ICT environments up and running and working as their main focus – while IT Managed Security Service Providers (MSSPs) are the “checkers”, making sure that things are running as securely as they need to be based upon business risk tolerance. While they both work on the same systems, their approach and the outcomes of their services are entirely different.
What we've seen in practice is that IT providers can often put the emphasis on the wrong security controls or turn on all the controls, thereby making security so complex that people find ways around them (making them ineffective). However, effective IT Security providers will assess how they can implement cybersecurity controls, policies, and procedures to enable business activities whilst also maximising security.
Often IT teams are under immense pressure “just to get things working”, and security concerns go either unnoticed, while the risks associated with the approach may not be fully understood, or sometimes are not correctly communicated to management so that risk thresholds can be assessed. IT Security are focused on risk based on business objectives, factors such as organisation's size and the industry being operated in, and use their knowledge of threat activities and vectors to guide the business on where they should focus their security efforts.
What it Means:
None of this means that organisations shouldn’t be using IT MSPs. In an ideal world, either an IT MSP will work together with a partner IT MSSP or encourage the companies they work with to engage with their own security provider in order to ensure both the doing and the checking aspects are covered. Expecting traditional IT providers to be security experts is likely to lead to serious problems that could be avoided by engaging specialists on both sides.
Need to talk about your security needs? Contact us and one of our friendly and knowledgeable team will be happy to help.
.png?width=400&height=53&name=logo%20(1).png)

.png?width=423&height=56&name=logo%20(1).png)