Cyber Security - Year In Review 2023
by Alex W, on 17/11/2023 4:18:03 PM
The statistics provided in the Australian Signals Directorate Cyber Threat Report paint a bleak picture of the cybersecurity landscape in Australia with the average cost of an incident and the frequency of incidents rising. Here are some added insights from the Security Centric team.
Key takeaways from the report include the following:
- State-based actors are focused on critical infrastructure – data theft and the disruption of business are key goals. Federal government remains the single largest reporter of cyber incidents to ASD.
- Small and Medium sized organisations are a being heavily targeted and had a much higher incidence of full compromise than larger organisations.
- Email compromise is the leading attack vector, when combined with business email compromise fraud it makes up over 25% of all incidents.
- Patching remains a critical issue with many incidents occurring AFTER a patch or mitigation was available. Of most concern being that 2 in 5 vulnerabilities (and the related incident reported) were exploited more than one month after a patch or mitigation advice was released.
Total of 1,134 Incidents Reported to ASD
As the statistics indicate, a large number of incidents impacted small and medium sized organisations. This follows a trend that Security Centric is seeing in the field of ‘soft targets’ being a victim of choice for opportunistic cyber criminals.
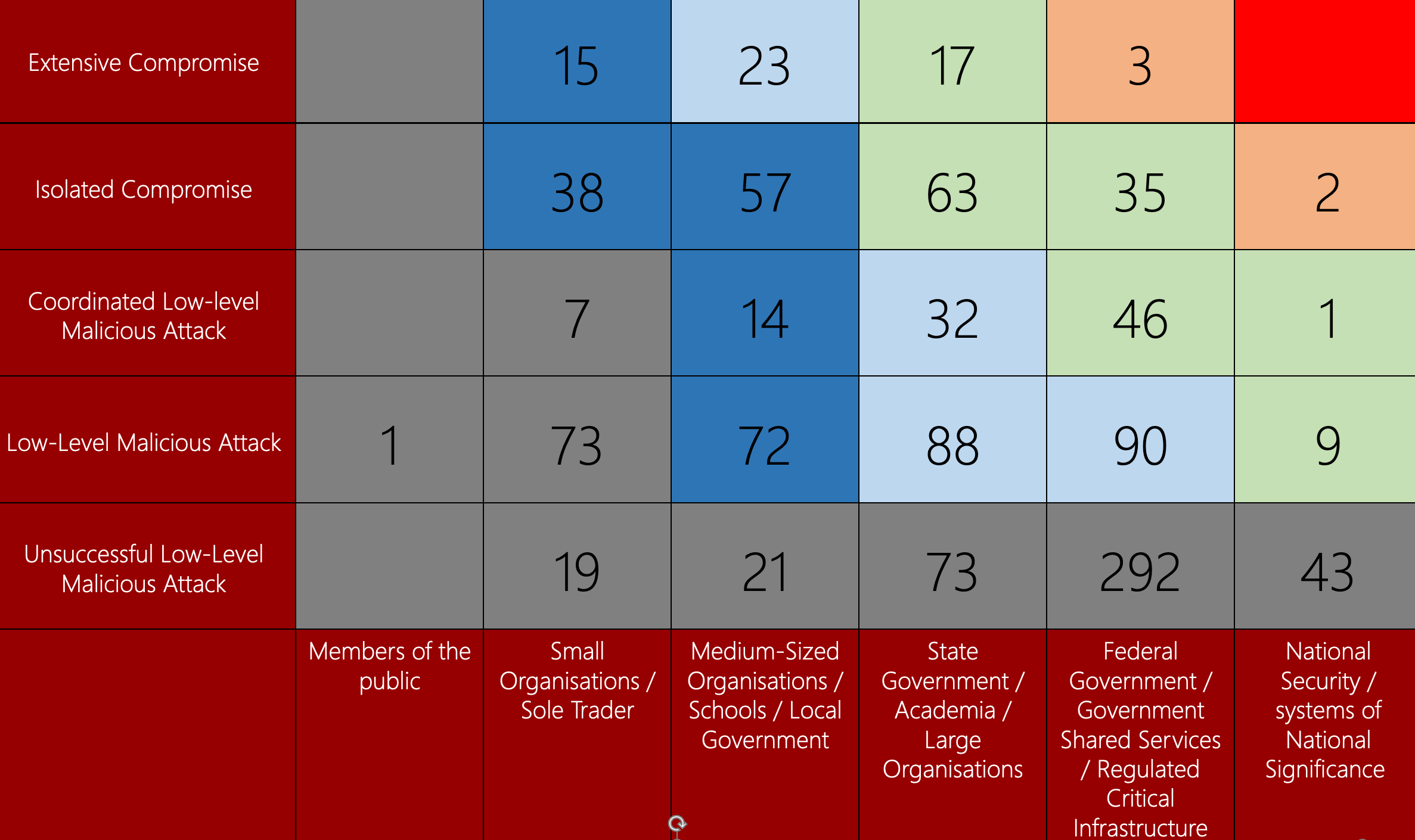
As governmental and large private organisations are heavily investing in cybersecurity, criminals will turn to easier targets that can still turn them a profit.
Operating in a sector that has not previously been targeted or believing that you are too small an organisation to be a worthwhile target is not a valid defense strategy.
Vulnerabilities - Worrying Trends
Worrying statistics in relation to exploits utilised in carrying out attacks were presented in the report. They represent immaturity in vulnerability identification as well as patching capability (and perhaps remediation prioritisation) across the organisations that were compromised.
In addition to information relating to criminals' preference for remotely exploitable vulnerabilities (our penetration testing team strongly agrees with this preference), the following statistics are very concerning:
- 1 in 5 vulnerabilities was exploited within 48 hours of a patch or mitigation advice being released
- half of the vulnerabilities were exploited within 2 weeks of a patch or mitigation advice being released
- 2 in 5 vulnerabilities were exploited more than one month after a patch or mitigation advice was released
Organisations will always have the risk of a ‘zero-day’ (essentially brand new vulnerabilities being utilised in the wild for the first time) attacks causing a compromise
‘Aged’ vulnerabilities however, especially those older than a month should not be ignored as they account for 40% of compromises.
As mentioned previously these statistics are for vulnerabilities that had patches or other mitigations available that were not treated.

A robust vulnerability managed program is needed to stay on top of the myriad of applications and operating systems in use within organisations.
Programs should include regular scanning as well as the often overlooked aspect of the prioritisation identified vulnerabilities for remediation. This helps to ensure that the often limited resources available are used effectively for patching activities.
Technical solutions are available to assist in this respect, however expertise in implementation and prioritisation is essential to manage vulnerabilities effectively.
.png?width=400&height=53&name=logo%20(1).png)

.png?width=423&height=56&name=logo%20(1).png)
